In the digital era, where the virtual space serves as both our playground and workplace, securing our online assets is crucial. Brute force attacks pose a significant threat to websites. As we explore how to protect your login page, we aim to provide owners with the latest tools and tips for effective brute force attack protection to defend against these attacks.
Understanding Brute Force Attacks
This section aims to explain how these attacks work, the risks they bring, and why it's crucial to have strong protection in place. Understanding brute force attacks is like having a key to building a stronger lock for your digital doors, keeping your online space safe from these continuous and determined attempts to gain unauthorized access.
What is a Brute Force Attack?
Brute force attacks pose a significant threat to the security of WordPress websites. Firstly, it's crucial to understand what a brute force attack entails. A brute force attack is a method cybercriminals use to gain unauthorized access by systematically trying all possible combinations of passwords. Moreover, these attacks can exploit vulnerabilities in login pages and compromise weak passwords.
So, why is brute force attack protection essential for WordPress users? Because website owners need to be aware of the common methods employed by attackers during brute force attempts.
Furthermore, understanding the mechanics of brute force attacks is integral to implementing effective protection measures. By examining the intricate details of these attacks, website administrators can better grasp the specific areas that require reinforcement. In addition, recognizing the targets of brute force attacks is key to developing a comprehensive security strategy.
Common methods of Brute Force Attacks
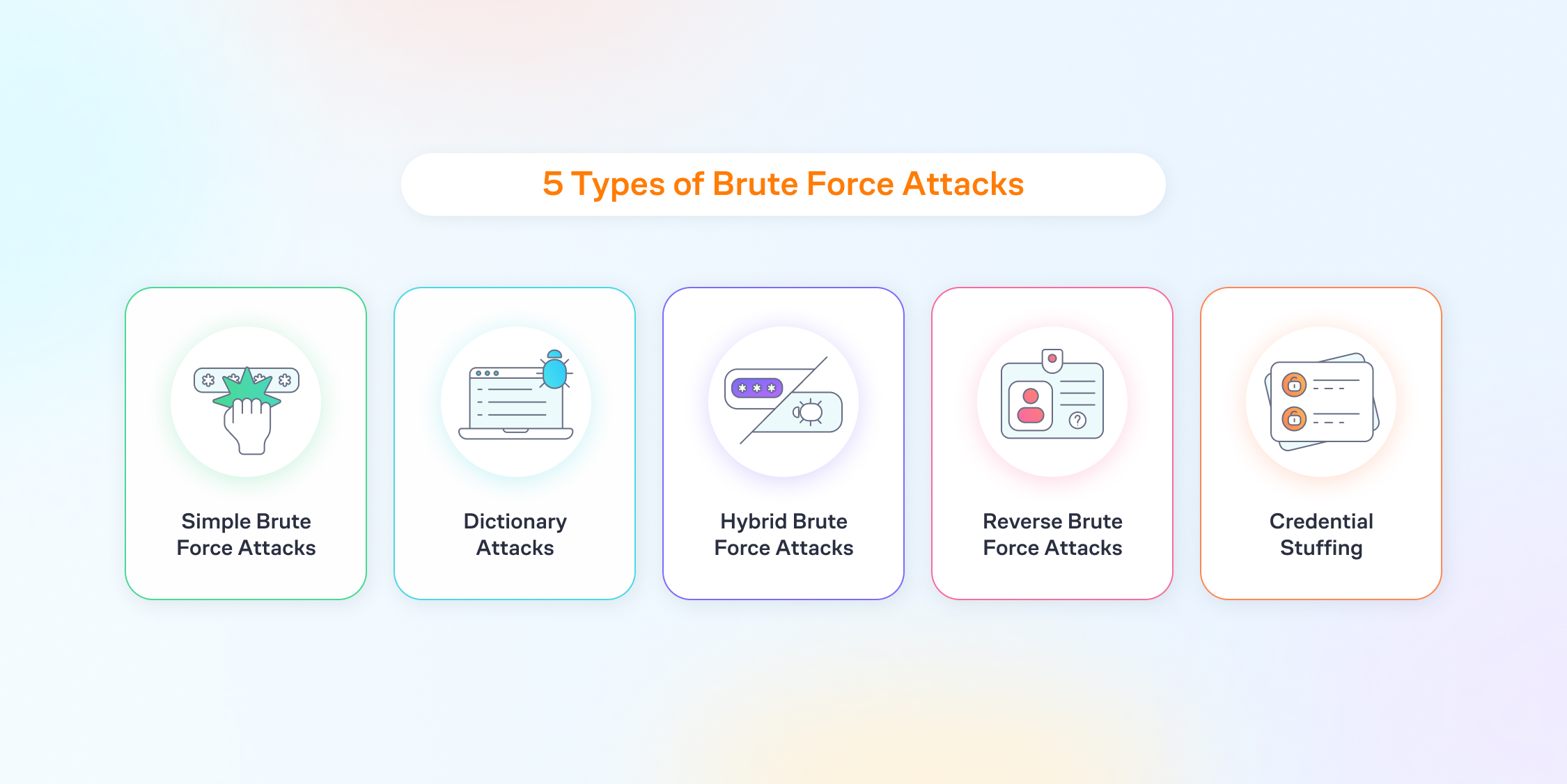
In the beginning, brute force attackers often rely on the straightforward method of systematically trying every possible password until the correct one is found. This method is time-consuming, yet effective if left unaddressed. Moreover, attackers frequently exploit weak and easily guessable passwords, especially now that AI tools are become more intelligent by the day.
Furthermore, attackers leverage dictionary attacks, wherein they systematically test all words from a pre-existing list of commonly used usernames and passwords. This method capitalizes on individuals' tendency to choose usernames and passwords that are easily memorable but, regrettably, also easily guessable.
Besides dictionary attacks, attackers employ credential stuffing, a technique where login credentials obtained from one platform are used to gain unauthorized access to another. This method preys on users who use the same credentials across multiple sites, underscoring the need for unique and varied passwords.
Moreover, attackers may resort to rainbow table attacks, where precomputed tables of hashed passwords are compared against the target system. Employing strong cryptographic hashes and salting passwords are essential deterrents to this method.
In addition to these nefarious techniques, attackers often capitalize on the oversight of poorly implemented account lockout policies. Neglecting to implement measures that limit the number of login attempts can inadvertently provide cyber assailants with the opportunity to launch undetected brute force attacks.
Hundreds of Agencies Across The World Use LLAR





Common Vulnerabilities in Brute Force Attacks
Some of the common issues that leave us vulnerable will also help us see how these attacks will target us and how we can better protect our websites. By examining these vulnerabilities, we can be smarter about keeping our accounts safe from cyber crimes that aim to guess our passwords.
Exploiting Weak Passwords
In the realm of online security, safeguarding your website from potential threats like brute force attacks is everything. Brute force attacks, particularly those targeting weak passwords, pose a significant risk to your website's integrity. To fortify your defenses, implementing measures against exploiting weak passwords is crucial for overall brute force attack protection.
1. Encourage Users To Create Strong Passwords
First and foremost, encourage users to create strong, complex passwords. Advising them to include a combination of uppercase and lowercase letters, numbers, and special characters enhances the password's resilience against brute force attempts. Equally important is educating users about the pitfalls of easily guessable passwords, such as common words or sequential numbers. In addition, be sure to never reuse passwords across your multiple accounts as hackers will try to use this to steal multiple of your accounts with hardly any extra work.
2. Implement Lockout Policies
Consider implementing account lockout policies. After a certain number of unsuccessful login attempts, temporarily lock user accounts. This not only acts as a deterrent but also hinders brute force attackers in their attempts to gain unauthorized access. Additionally, regularly audit and update your password policies to stay one step ahead of evolving cyber threats.
3. Multi-factor authentication
Invest in multi-factor authentication (MFA). Adding an extra layer of security by requiring users to verify their identity through multiple means significantly reduces the likelihood of successful brute force attacks. Besides, regularly monitor login activity and promptly address any suspicious behavior, further improving your website's defenses.
Identifying Login Page Vulnerabilities
One crucial aspect of this defense is identifying vulnerabilities within your login page. Effective protection begins with a comprehensive understanding of potential weak points.
From the start it is important to scrutinize your password policy. A strong password policy acts as an initial barrier against brute force attacks. Ensure that your system mandates complex, unique passwords and implements multi-factor authentication (MFA). This not only fortifies your defenses against traditional password-guessing methods but also adds an extra layer of security.
Furthermore, monitor login attempts diligently. Implementing account lockout policies, which temporarily suspend access after a specified number of unsuccessful login attempts, is a strategic move. This measure thwarts brute force attackers by impeding their repeated efforts. Additionally, log and analyze login activity regularly to detect any unusual patterns or suspicious IP addresses.
Lastly, consider deploying web application firewalls (WAFs) for an added layer of defense. WAFs scrutinize and filter incoming traffic, identifying and thwarting malicious attempts before they reach your login page.
Choosing the Right Tools for Brute Force Attack Protection
To protect our online spaces, it's important to choose the right tools. This means picking the tools that can stop these attacks and adapt to new tricks hackers might use. This section is all about how to make the smart choice in tools for keeping our online accounts secure from these sneaky attacks.
Overview of Brute Force Protection Plugins
One effective line of defense involves the use of Brute Force Protection Plugins. These specialized tools act as digital guardians, fortifying your website against unauthorized login attempts and bolstering its overall security.
What's noteworthy about these plugins is their ability to monitor login activities in real-time. They analyze login attempts and swiftly identify patterns indicative of a brute force attack. Next, they employ advanced algorithms to distinguish between legitimate users and malicious actors attempting to gain unauthorized access.
Besides real-time monitoring, these plugins often offer an array of customizable settings. Website administrators can set thresholds for login attempts, after which the plugin may initiate protective measures. This not only thwarts potential attacks but also provides a level of adaptability that is crucial in the ever-evolving landscape of cyber threats.

Key Features to Look for in a Security Tool
When selecting a security tool to fortify your online presence, it's crucial to pay attention to key features that can make a significant difference in safeguarding your sensitive data.
1. Opt for Multi-Factor Authentication (MFA)
An effective security tool should offer multi-factor authentication as a first line of defense. MFA adds an extra layer of protection by requiring users to verify their identity through multiple means, thwarting unauthorized access attempts.
2. Real-time Monitoring and Alerts are Essential
The ability to monitor your website's activities in real-time is equally important. An advanced security tool should provide real-time alerts, allowing you to respond promptly to any suspicious activities or potential brute force attacks. This proactive approach can prevent security breaches before they escalate.
3. Complex Password Policies
A security tool with complex password policies is a must. Ensure that the tool enforces complex password requirements, limiting the effectiveness of brute force attacks attempting to crack login credentials.
4. IP Blocking and Rate Limiting Features
To add an extra layer of defense against brute force attacks, opt for a security tool that includes IP blocking and rate limiting features. These capabilities prevent repeated login attempts from the same IP address, making it significantly more challenging for attackers to gain unauthorized access.
5. Seamless Integration with Content Delivery Networks (CDNs)
Consider a security tool that seamlessly integrates with Content Delivery Networks. This integration optimizes the distribution of your website's content while providing an added layer of security against brute force attacks.
Installation and Configuration
Securing your website against potential threats, especially brute force attacks, is crucial in today's digital landscape. A formidable line of defense comes in the form of powerful security plugins. In this step-by-step guide, we will walk you through the process of installing a brute force security plugin, an essential component of comprehensive brute force attack protection.

Step-by-Step Guide to Installing A Brute Force Security Plugin
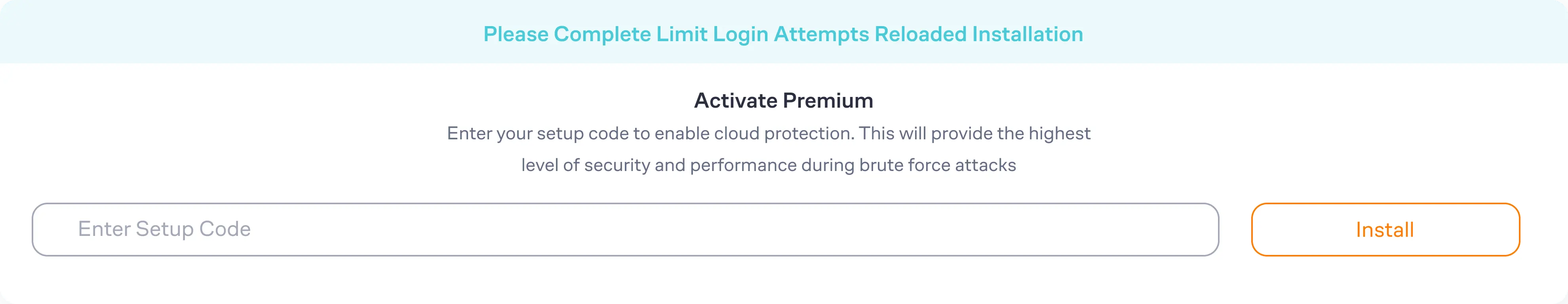
Firstly, Identify a reputable security plugin that suits your website's platform. For WordPress users, a popular choice is the Limit Login Attempts Plugin. Navigate to your website's admin dashboard and locate the plugin section.
Next, click on the "Add New" button and search for your chosen security plugin. Click "Install Now," and once the installation is complete, click "Activate." This initiates the integration of the security plugin into your website.
Lastly, configure the plugin settings to align with your security preferences. This may include setting up login attempt limits, IP blocking rules, and other advanced features that enhance your website's security posture.
Configuring Settings for Optimal Brute Force Attack Protection
After installing and activating the Limit Login Attempts Reloaded plugin, the required settings will configured by default. However there are a few recommendations to bolster your login security and make the protection more effective.
1. Safelist your username and IP address (Free version)
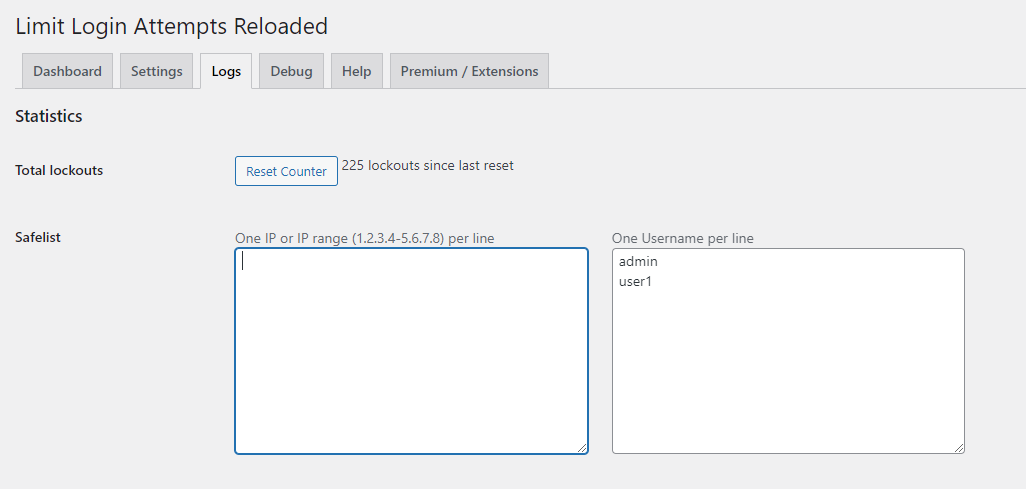
Within the plugin dashboard, navigate to the Logs tab and input all your usernames into the safelist field. This action guarantees your legitimate users will not get locked out. If your Internet Service Provider (ISP) assigns you a static IP address, include it in the IP field to permit login attempts solely from that address. However, if your IP is dynamic or you log in from various locations, refrain from entering anything in this field.
2. Block XMLRPC & Auto-Add IPs to Blocklist (Premium)
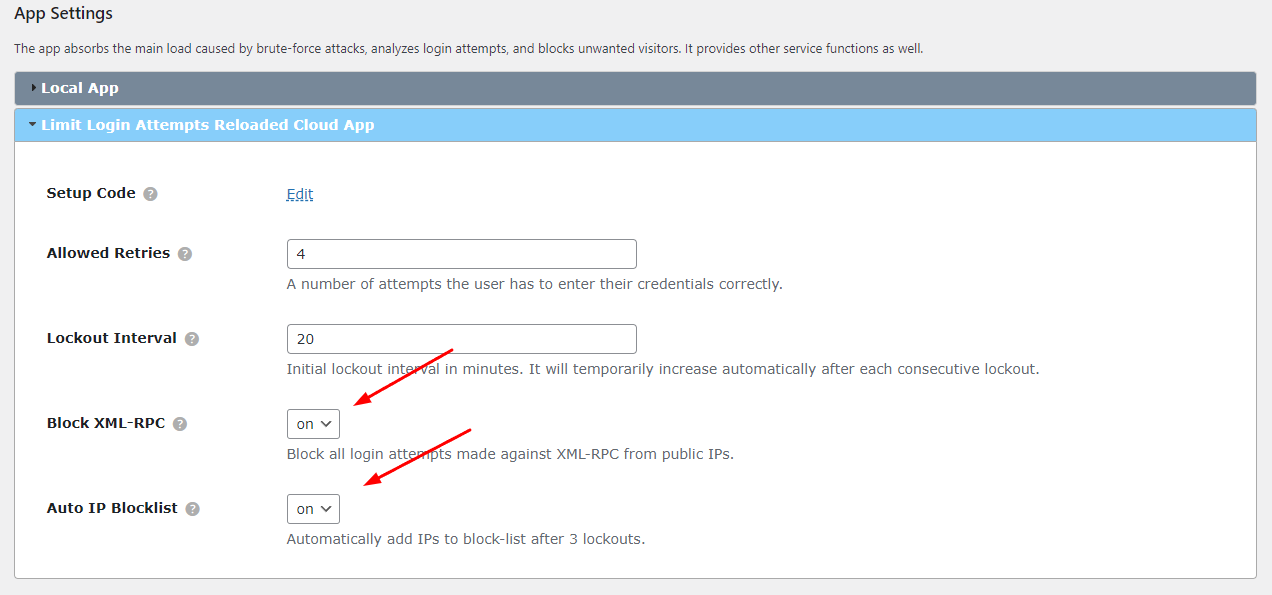
Blocking XML-RPC (XML Remote Procedure Call) on websites is often done for security reasons. XML-RPC is a protocol that allows remote communication between different systems over HTTP. While XML-RPC itself is not inherently insecure, it has been exploited in the past, leading to potential security vulnerabilities. In addition, it's highly suggested to add IPs to the blocklist if they have 3 consecutive lockouts. It's important to make sure both of these features are enabled.
3. Deny/Allow Countries (Premium)
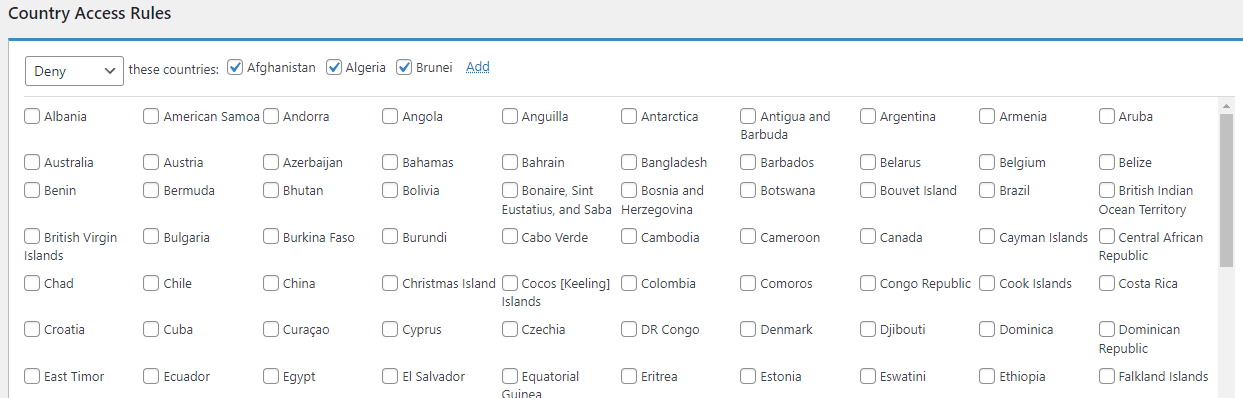
Users who opt for the Limit Login Attempts Premium can restrict access by country, effectively reducing the number of login attempts. Navigate to the Login Firewall tab, and in the Country Access Rules section, choose to either deny or allow specific countries according to your preferences.
Additional Security Measures
When it comes to keeping websites safe from brute force attacks, it's not just about having the right tools. We also need extra security measures to make sure our defenses are strong. This part of the article talks about some additional things we can do to protect our websites. It's like adding extra layers of security beyond the basic tools.
Creating Password Policies for your Company
In the ever-evolving landscape of cybersecurity, establishing robust password policies is a critical component of a comprehensive brute force attack protection strategy. By fortifying your company's defenses with stringent password guidelines, you create an essential barrier against unauthorized access.
1. Set minimum password length requirements
A longer password is inherently more secure, thwarting brute force attempts by increasing the number of possible combinations. Moreover, incorporating a mix of uppercase and lowercase letters, numbers, and special characters enhances complexity, making it harder for malicious actors to crack passwords.
2. Consider implementing regular password updates
Enforcing periodic changes ensures that even if a password is compromised, the window of vulnerability is minimized. Encourage employees to avoid using easily guessable information, such as birthdays or common words, and instead opt for unique combinations.
3. Educate your team on the significance of avoiding password reuse
When an individual utilizes the same password across multiple platforms, a breach on one site exposes all associated accounts. By instilling a culture of password uniqueness, you fortify your company's defenses against widespread attacks.
4. Implementation of account lockout policies
Limit the number of unsuccessful login attempts to counter brute force attacks. This preventative measure not only mitigates the risk of unauthorized access but also signals potential security threats, allowing for timely intervention.
Regular Monitoring and Updates for Continued Protection
In the ever-growing world of online security, safeguarding your website from potential threats like brute force attacks is an ongoing process that requires vigilance and strategic planning. Regular monitoring and updates play a pivotal role in fortifying your digital defenses and ensuring the longevity of your brute force attack protection measures.
Firstly, implementing a complex monitoring system is imperative. By monitoring your website's logs and traffic patterns, you can swiftly identify any unusual activities that may signal a potential brute force attack. Early detection is key to preemptive action and can save your website from falling victim to malicious attacks.
Moreover, staying on top of the latest security updates is equally important. Software developers continually release patches and updates to address newly discovered vulnerabilities. By promptly applying these updates, you not only enhance your website's resilience but also stay one step ahead of cyber threats. Incorporating automated tools for monitoring and updates can streamline the process. Automated systems can efficiently scan for vulnerabilities and apply patches, reducing the risk of human error and providing real-time protection.
Conclusion
Regular monitoring and updates are crucial in the ongoing battle for effective protection against brute force attacks. When looking at online security where threats are evolving continuously, the vigilance and strategic planning embedded in this approach are essential. Quick detection through strong monitoring systems enables preemptive action against potential attacks, ensuring website safety from malicious attacks. Equally important is the continuous adoption of the latest security updates, acting as a proactive shield against emerging vulnerabilities. By following a consistent update schedule and utilizing automated tools, website owners strengthen their digital defenses with real-time protection. The synergy between constant monitoring and timely updates serves as a strong defense strategy, reinforcing the digital defenses against the constant threat of brute force attacks.
Frequently Asked Questions
Brute force attacks happen regularly on the internet. The frequency varies based on factors like how popular a website is and how strong its security is. Websites with weak passwords are more at risk. To protect against brute force attacks, use strong passwords, enable multi-factor authentication, and keep software updated.
Brute force attacks can compromise the security of systems by gaining unauthorized access through repeated login attempts. Protecting against such attacks is crucial to prevent unauthorized access and potential data breaches.
Brute force attacks can come from anywhere in the world. Cyber criminals might control networks of compromised computers or use anonymous networks to hide. The attacks can also involve infected devices or hired services. It's hard to trace where they come from exactly. So, it's important to have strong security measures in place to defend against these attacks, no matter where they originate.
Users can enhance their protection by using strong, unique passwords, enabling multi-factor authentication whenever possible, keeping software and systems updated, and being vigilant about phishing attempts that could compromise login credentials.