When it comes to keeping your WordPress site safe, there is a long list of things you could be doing. But if you are not paying attention to login security, then the rest of your security strategy will not matter all that much.
Let me put it this way. If someone gets past your login screen, they are already inside the house. At that point, it is not about keeping them out. It is about damage control.
Whether you are running a small blog or managing a high traffic eCommerce site, the login page is one of the most targeted entry points for attacks. And if you are not doing anything to protect it, you are leaving the front door wide open.
Let’s walk through what login security actually means, how to know if your site is being targeted, and what you can do today to lock it down. I will also show you how Limit Login Attempts Reloaded (LLAR) helps make this process easier and more effective without slowing down your site or making it hard to manage.
What Is Login Security and Why Should You Care?
Login security is exactly what it sounds like. It is the layer of protection between your WordPress login screen and someone getting access to your dashboard.
But here is the thing. Most people assume that a good password is enough. It is not. Hackers are not sitting there manually guessing your login. They are using bots to throw thousands of attempts per minute at your site. This is called a brute force attack, and unless you have taken steps to block it, they can keep hammering away until something works.
If they get in, it is game over. That one vulnerability can lead to:
- Malware injected into your files
- Your search rankings dropping because your domain gets flagged
- Spam links scattered across your pages
- Customer data being exposed
- And hours or even days of cleanup
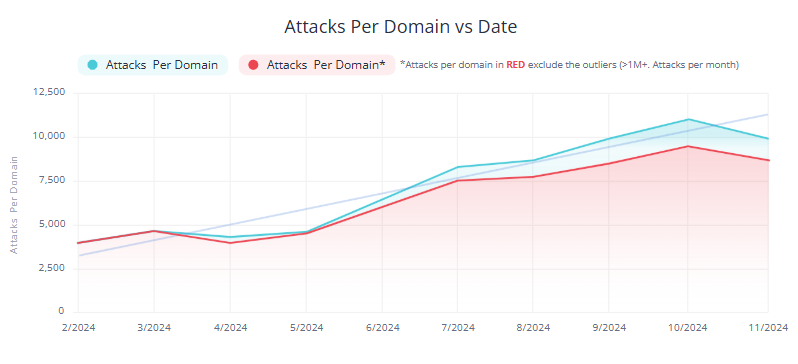
According to our State of Brute Force Attacks in WordPress – 2025 report, over 82 percent of all login attempts recorded in 2024 were unauthorized. That is millions of attempts across thousands of sites—most of which were automated and relentless.
This is not paranoia. It is the reality of running a WordPress site today.
Signs Your Login Page Is Being Targeted
You do not need to be a cybersecurity expert to know something shady is going on. If you have ever seen any of the following signs, there is a good chance your login page is under attack:
- Lots of failed login attempts with random usernames
- IP addresses from unknown countries trying to log in
- Sudden slowdowns on the login screen
- Successful logins at strange hours that you do not recognize
One of the best ways to stay ahead of this is to track login activity, including both failed and successful logins. That is where Limit Login Attempts Reloaded really shines.
With LLAR, you can see who is logging in and when. You can also get notified the moment something suspicious happens and lock out bad actors before they can do damage. It is straightforward, reliable, and does not require a technical background.
Our research shows that bots can try anywhere from 300 to 1,200 password combinations per minute, depending on the server they are hitting. That is why having a login limit in place is one of the most effective defenses—it stops the attack before it gains momentum.

What Most WordPress Users Get Wrong About Login Security
There are a few common myths that get people in trouble.
Myth 1: "I have a strong password, so I am fine"
A strong password is a great first step, but it is not enough. If someone finds a weak plugin or guesses your username, it might not matter. You need layers of protection.
Myth 2: "No one would ever target my small site"
This is a big one. Hackers are not just going after big brands. They use bots that scan thousands of sites a day, looking for easy entry points. Smaller sites often get hit because they have weaker defenses.
Our data shows that the majority of brute force activity targets low traffic or personal sites, not big commercial blogs. That is because these sites are less likely to be monitored or protected.
Myth 3: "I will deal with it if something happens"
By then, it is too late. Cleaning up a hacked site takes time, money, and energy. It is always easier and cheaper to prevent the problem in the first place.
How Limit Login Attempts Reloaded Improves Login Security
Let’s talk about what LLAR actually does to protect your site. If you are already using it, great. If not, you are missing out on some of the most effective tools for securing your login page.
1. Stop Brute Force Attacks with Login Limits
LLAR limits how many login attempts are allowed from a single IP address. Once that number is reached, the user is locked out. This blocks brute force bots from getting unlimited tries.
This one setting alone helps block over 4.2 million attacks per month across the LLAR user base, according to our internal telemetry.
2. Get Real Time Email Notifications
You can set up LLAR to send you an email the second someone is locked out. That way, if someone is repeatedly trying to break in, you will know right away.
3. Track Successful Logins
Not only does LLAR track failed logins, but it also logs successful ones. You can see who logged in, when they logged in, and from where. If someone logs in and you do not recognize it, that is a red flag you can act on immediately.
4. Customize Your Lockout Rules
LLAR gives you full control over how strict or relaxed your security is. You decide how many failed attempts trigger a lockout, how long that lockout lasts, and whether to notify the user.
5 Things You Can Do Right Now to Strengthen Login Security
Step 1: Change the Default Admin Username
If you are still using “admin” as your username, change it. Create a new admin account with a unique username, transfer everything to that account, and delete the old one.
Step 2: Use a Strong, Unique Password
Use a password manager and generate something long and random. Do not write it down, and do not reuse it anywhere else.
Step 3: Install Limit Login Attempts Reloaded
This takes less than a minute and gives you an immediate boost in login protection. Start with the default settings, then adjust as needed.
Step 4: Monitor Login Logs Regularly
Check your LLAR logs weekly. Look for strange IP addresses, logins from unfamiliar locations, or failed attempts at odd times.
Step 5: Keep Your Site Updated
Make updating plugins, themes, and WordPress core a habit. Outdated software opens the door to all kinds of exploits.
Wrapping It Up
Login security is not a feature. It is a necessity. As attacks become more frequent and more automated, protecting your login page is one of the smartest things you can do for your WordPress site.
Limit Login Attempts Reloaded is a lightweight, powerful tool that makes login security easier to manage. It limits failed attempts, notifies you when something is off, and helps you track who is getting into your site and when.
If you are serious about keeping your site secure, start with your login page. Everything else builds from there.
Want to dig deeper?
Read the full State of Brute Force Attacks in WordPress – 2025 to learn how these threats are evolving and what you can do to stay ahead.
Need help getting started with LLAR?
Sign up for FREE from the WordPress plugin marketplace or explore the premium features for even more protection.